A friend sent me this message from one of the groups she was on:
I’ve just found out that chats in Telegram (unlike in Signal) are not encrypted by default (unless started as secret chat) and group chats are not encrypted at all!”
and asked if this was true.
I think terms like “not encrypted”, “end to end encryption” need to be understood better so we can make better decisions about what to use and not. Here’s what I wrote back:
“Yes, Telegram encryption works differently from Signal but it’s just plain inaccurate that Telegram chats are not encrypted. They are. Both “in transit” ie from your phone to Telegram and “at rest” ie on Telegram servers.
So what’s the difference between the apps?
Telegram chats are encrypted by Telegram’s keys, which are stored separately from the data. From their privacy policy:
Telegram is a cloud service. We store messages, photos, videos and documents from your cloud chats on our servers so that you can access your data from any of your devices anytime without having to rely on third-party backups. All data is stored heavily encrypted and the encryption keys in each case are stored in several other data centers in different jurisdictions. This way local engineers or physical intruders cannot get access to user data.
All group chats are also encrypted in the same way:
In addition to private messages, Telegram also supports public channels and public groups. All public chats are cloud chats (see section 3.3.1 above). Like everything on Telegram, the data you post in public communities is encrypted, both in storage and in transit — but everything you post in public will be accessible to everyone.
For 1:1 conversations, Telegram has what it calls ‘secret chats’, where the encryption keys are known only to the two devices – one for each person. Again from Telegram’s privacy policy:
[In secret chats] all data is encrypted with a key that only you and the recipient know. There is no way for us or anybody else without direct access to your device to learn what content is being sent in those messages. We do not store your secret chats on our servers. We also do not keep any logs for messages in secret chats, so after a short period of time we no longer know who or when you messaged via secret chats.
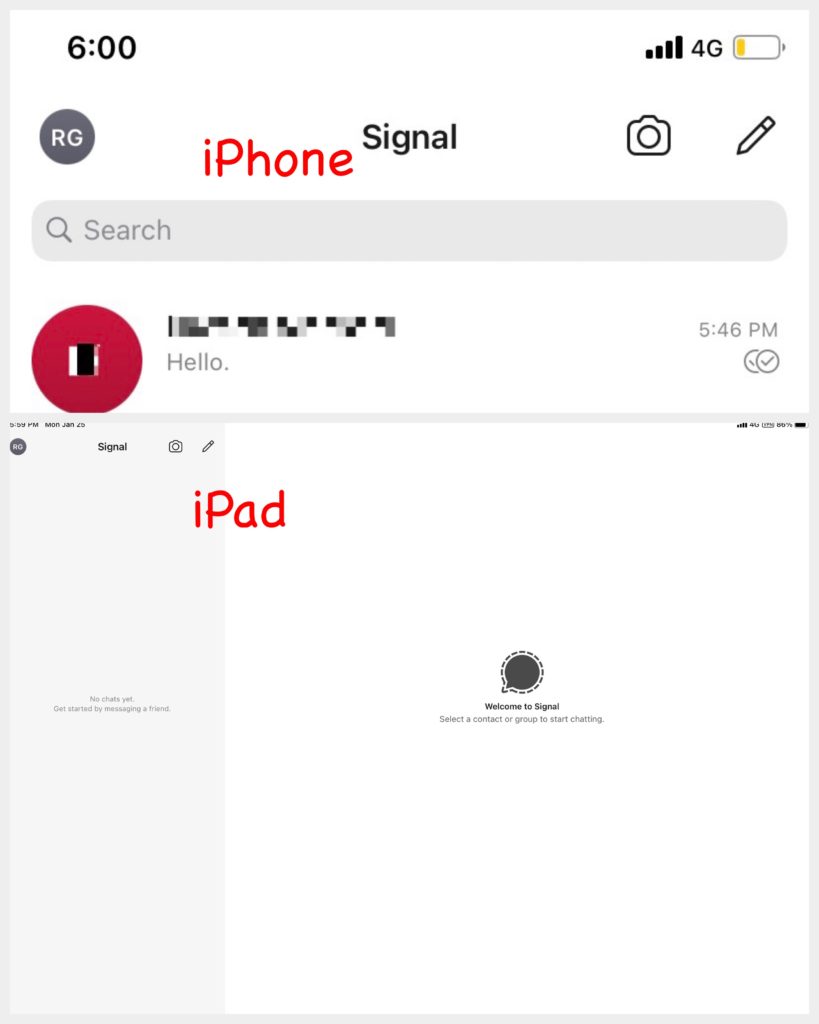
So if you only use Telegram on one iPhone and I use it on iPhone, iPad, and two Macs and I use each of them to chat with you, you will have four distinct ‘secret’ conversations with me on the same phone, and I will have one conversation with you on each of my devices, but all disjointed. In return, no messages are stored on Telegram’s servers.
Signal works this way by default – separate message queue for devices. You can see that the conversion on my iPhone is not synced to my iPad automatically:
But there is a tradeoff. Once again, Telegram’s privacy policy:
For the same reasons secret chats are not available in the cloud — you can only access those messages from the device they were sent to or from.
Without getting into the details, it’s really tough to do all three of the following:
- a. support perfect message sync between mutliple devices and
- b. encrypt it on-device and
- c. not store messages on the server.
With this model,
- Telegram does b. and c. for secret chats but sacrifices a. Signal works this way by default.
- Apple iMessage does a. and b. but does store messages on its servers for seven days, after which it deletes them, technically achieving c. but and sacrificing a.
- Whatsapp does b. and c. but doesn’t do a., which is why Whatsapp Web always needs to connect to your phone.
Hope this helps.”
I’m quite happy with the ongoing conversation around the loss of personal privacy online. There seems to be mainstream coverage of its pervasiveness for the first time, even if it’ll be churned away by the next news cycle.
But this conversation is as vulnerable to being hijacked and derailed by disinformation as any other. I think it’s important for those who can to explain technology and terminology in such a way that people can make educated decisions about reclaiming their privacy.