Earlier I described how a friend was tricked into losing control of her Whatsapp account and the damage that her attacker caused. I also showed, with screenshots, how you can protect yourself in under one minute by turning onWhatsapp’s two-step verification.
A scammer can use the same tricks against you on your other accounts, like your Gmail. Such attacks are more common than you think. According to this BBC article from April, Google was blocking 100 million phishing emails a day.
What does a Gmail phishing attack look like?
Phishing techniques improve every day, and are quite sophisticated even today.
You could get an email that looks like it’s from Google, but is not, asking you to tap a button – it could say it’s for account maintenance, to accept new terms and conditions, to download a Google Doc someone’s shared with you or a number of other things.
When you click on the button in the email, you get a screen that looks like this:
This screen looks like it’s from Google, but it isn’t. The only way to tell is by carefully looking at the URL (the web address in the bar). For most of us who are perennially distracted, it’s really hard to tell the difference.
You enter your username and your password, but it’s read by the attacker instead of by Google. You have lost control of your account. Your attacker can now use Google’s security features against you and log you out – from your browser, your Gmail app, Google Docs – everything.
If someone gets access to your Gmail account, or any other email account like Yahoo, Outlook or iCloud, they could then get into other your other accounts – Instagram, Facebook, Snapchat – by sending a password reset email to that email account, and then changing the password.
How do I protect Gmail – and my other accounts?
Gmail has support for two-factor-authentication, that is, support for a second layer of protection beyond your password/OTP.
This second layer is a six-digit code that you enter after you have entered your email address and password on a new computer/app install. So you see two login screens, one after another, instead of one.
As we will see in detail below, the scammer may be able to trick you into giving up your Gmail password, but it’s really hard for them to be able to get your two-factor code.
Not just Gmail/Google, here is a list of common accounts that you can and should enable this two-factor-authentication for:
- Gmail (or Google) account
- Apple iCloud account
- Snapchat
- Dropbox
But, you ask, how is it practical to remember six-digit codes for all these accounts? Surely it isn’t wise to use a single code for all these accounts.
That’s right. In fact, you don’t need to remember any of these codes at all.
You will use a new app, Authy, to generate new six-digit codes whenever you log into Gmail or these other accounts from a new phone or computer.
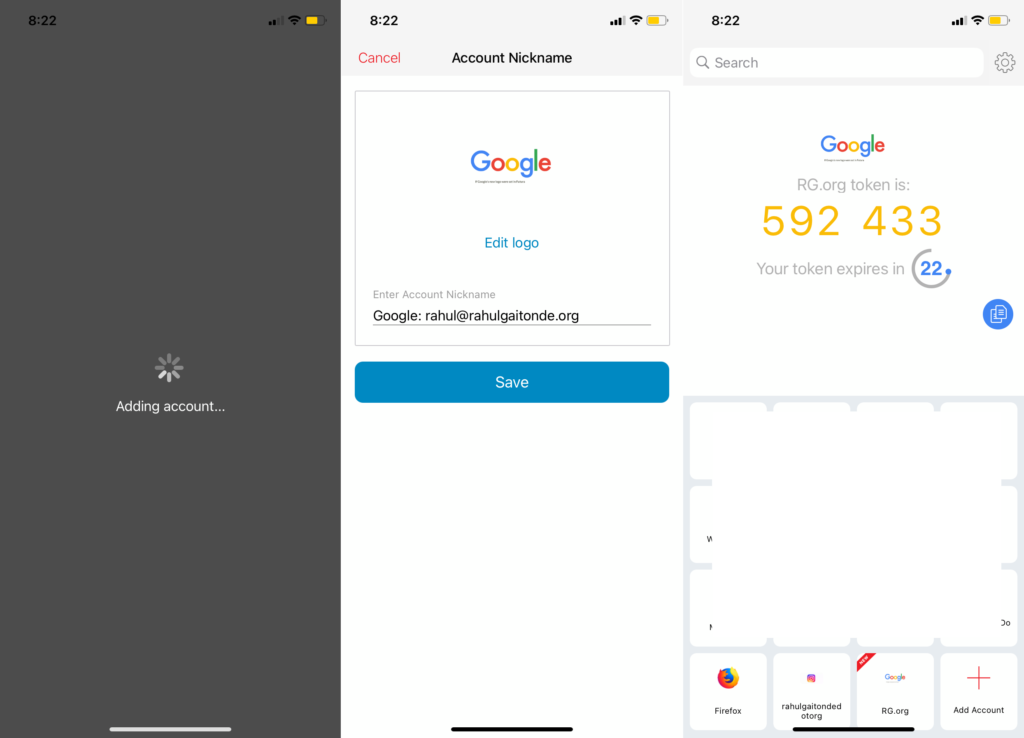
Authy is a dedicated two-factor-authentication app (now owned by the Internet infrastructure company Twilio.) You can see a screenshot of my own Authy app with two-factor set up for several accounts.
You can see that Authy’s auto-generated a code for one of my accounts which I can just type when I login. So I get the full benefit of this second layer of protection without remembering codes for any of these accounts.
You can install Authy on more than one device – say your iPhone and iPad. You can even install it on your desktop computers. You secure the app itself with an Authy password – which is the only password you need to remember (or store in your password manager).
Setting up your Gmail account with two-factor protection using Authy
Install the Authy app from the iOS App Store or the Google Play Store and sign up – this part should be super-simple.
Keep the following handy: the Gmail app on your phone. And a laptop browser window.
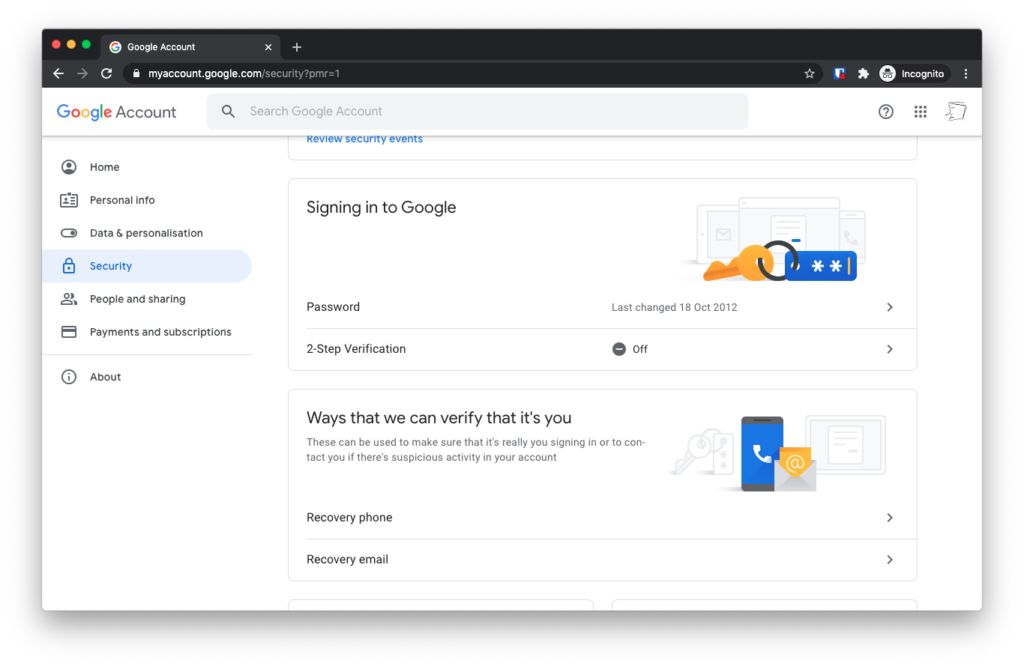
Now. Login to your Google Account Management page at accounts.google.com. Tap the “Security” section on the left. Scroll down to the “Signing in to Google?” section. You’ll see that “2-step verification’ is off. Click it.
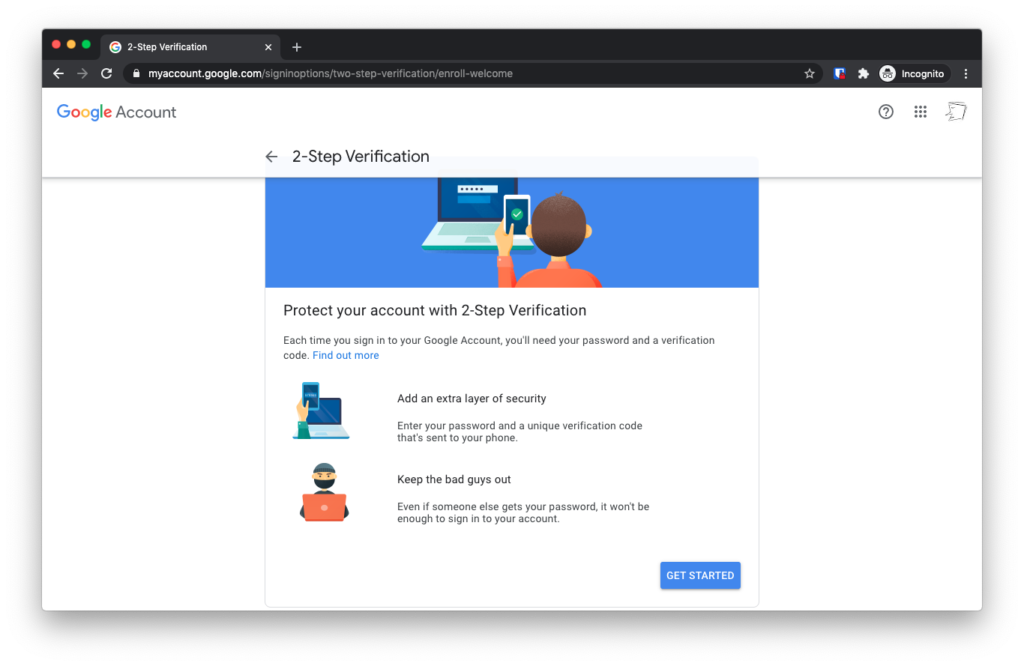
Now you’ll go through a simple wizard to set up your two-step verification. Tap Next on the Introduction screen:
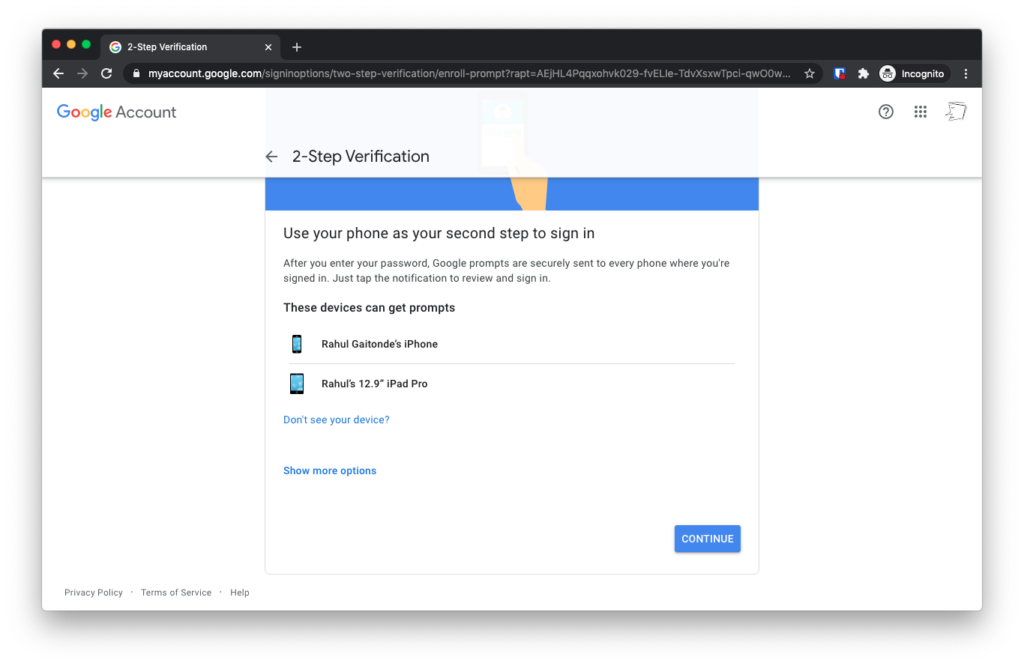
Tap “Continue” on the next screen, titled “Use your phone as your second step to sign in”
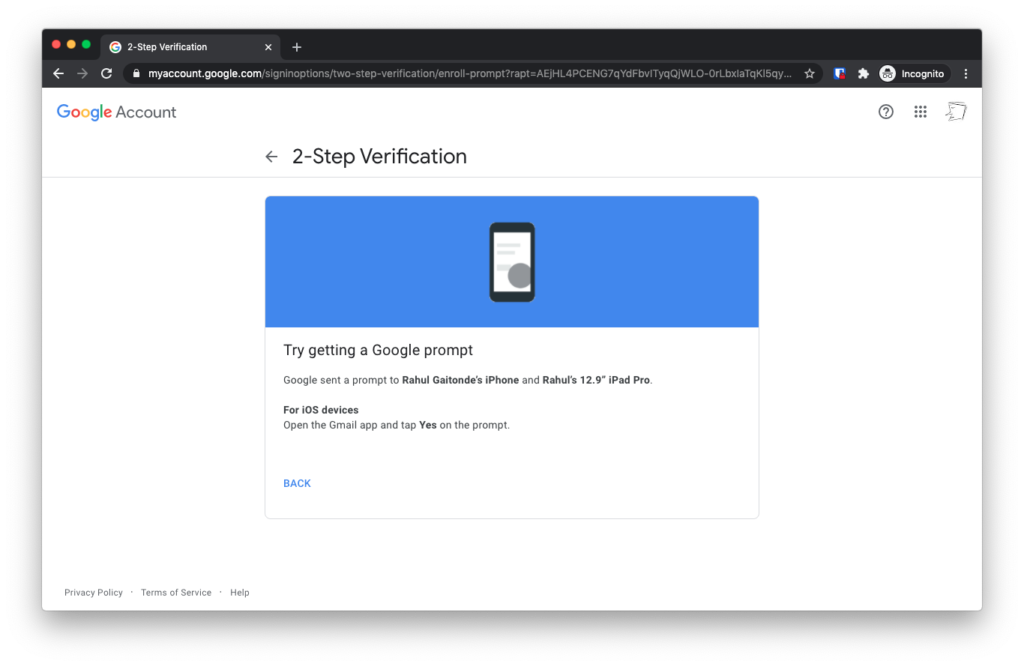
Now on the next screen, the wizard says that Google has sent a notification to your Gmail app.
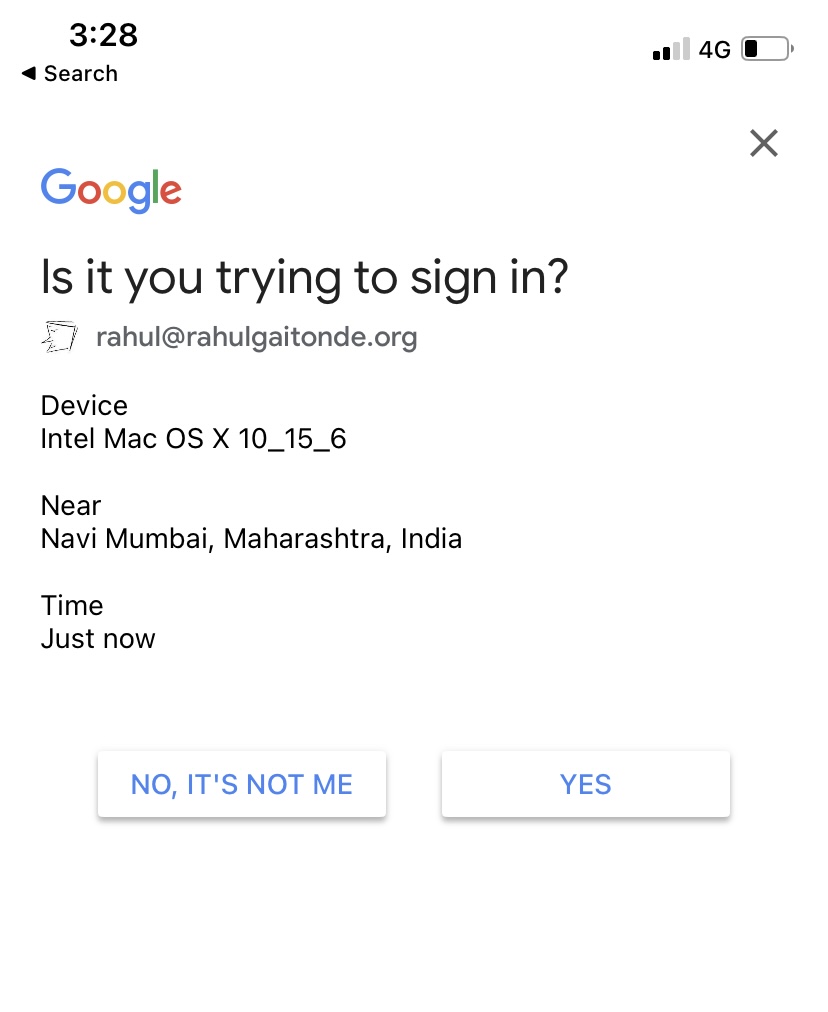
Launch the Gmail app on your phone and instead of your inbox, you’ll see a login notification. Tap Yes.
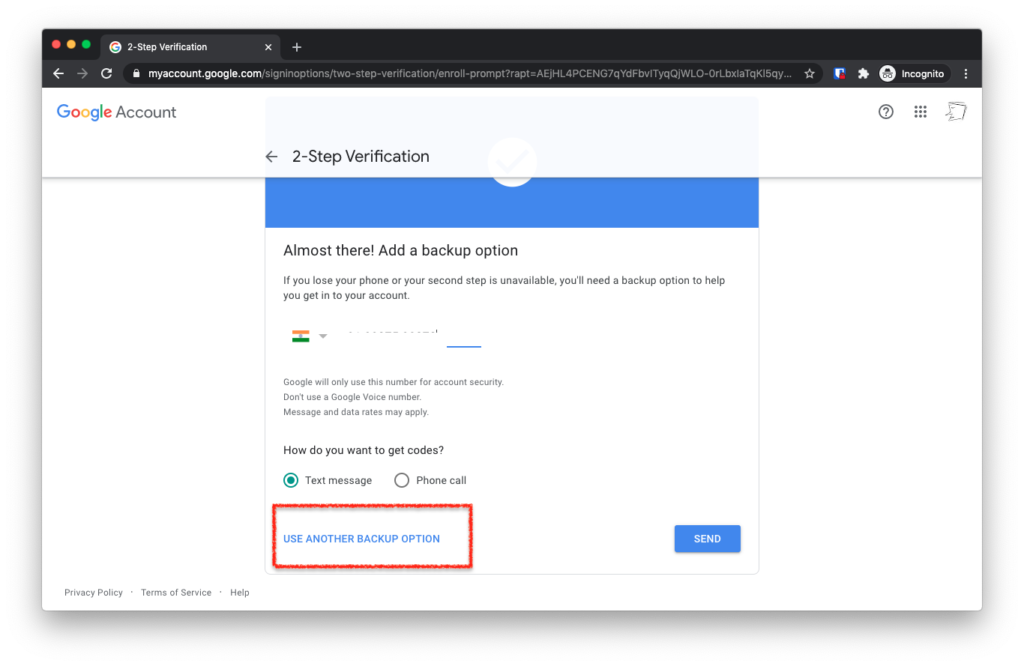
On the next screen, “Backup”, tap “Use another backup option”
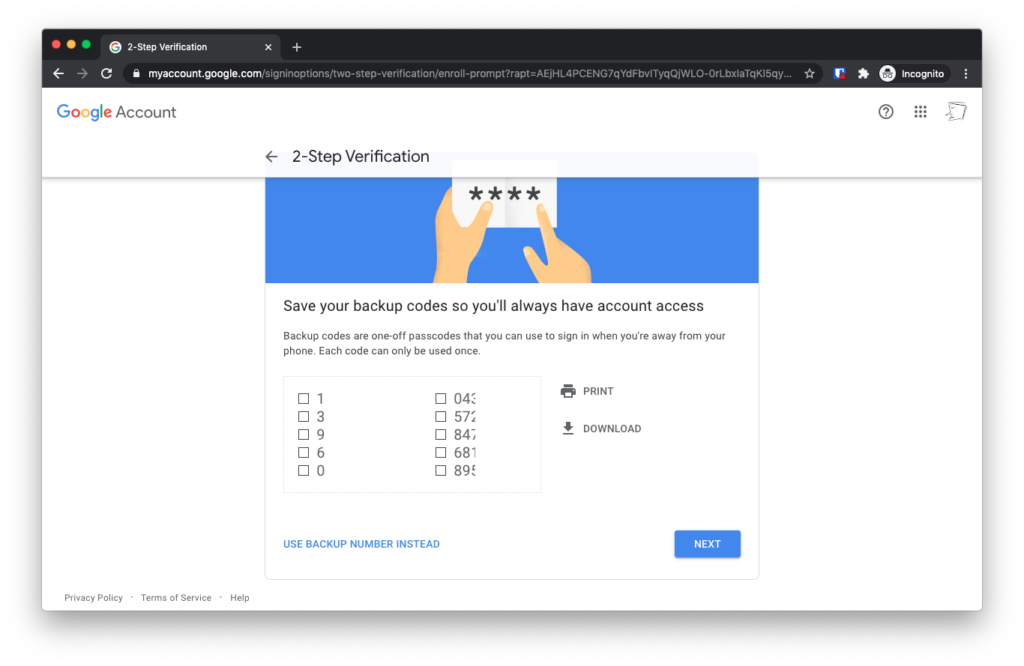
You’ll see a bunch of recovery codes. Tap “Download”. Rename the text file to “Gmail Recovery Codes” and save the file in your My Documents folder.
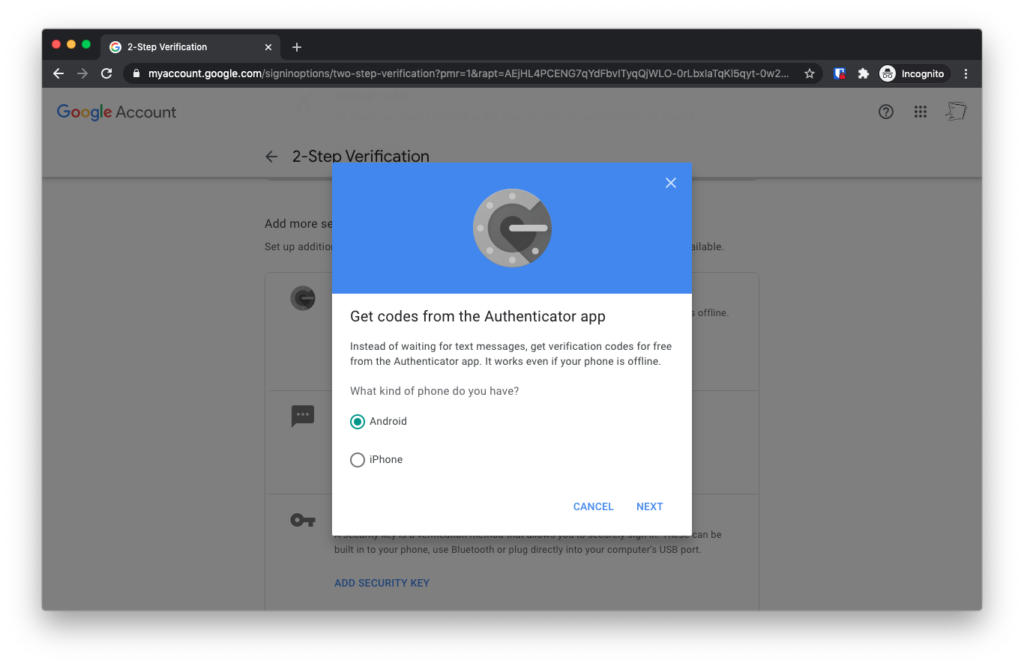
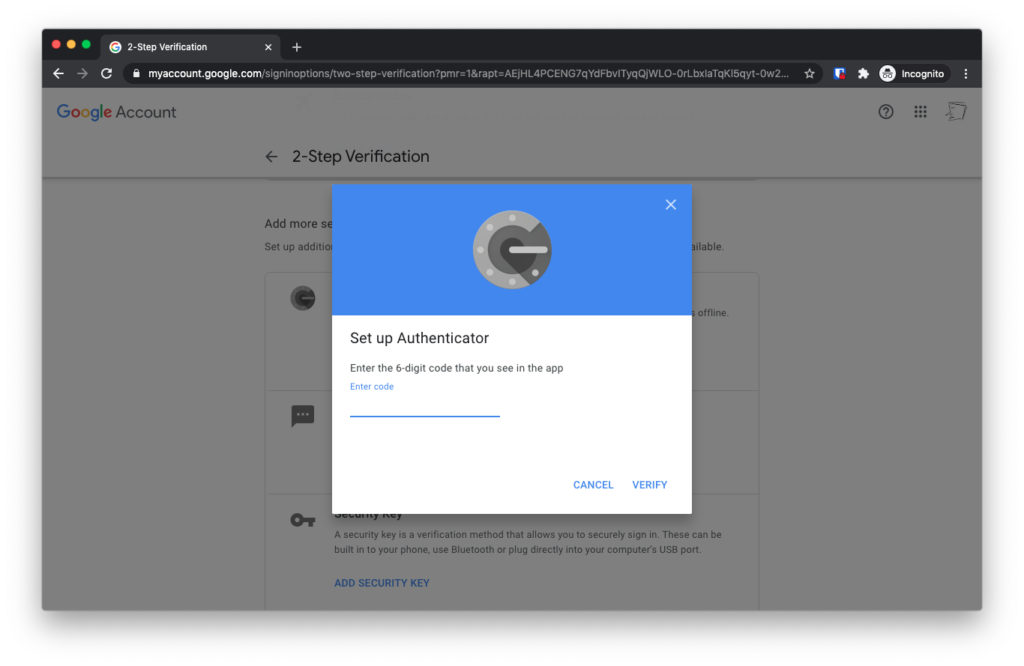
Just one more step: On the next screen, under the “Add more second steps to verify it’s you”, tap the “Authenticator App” section.
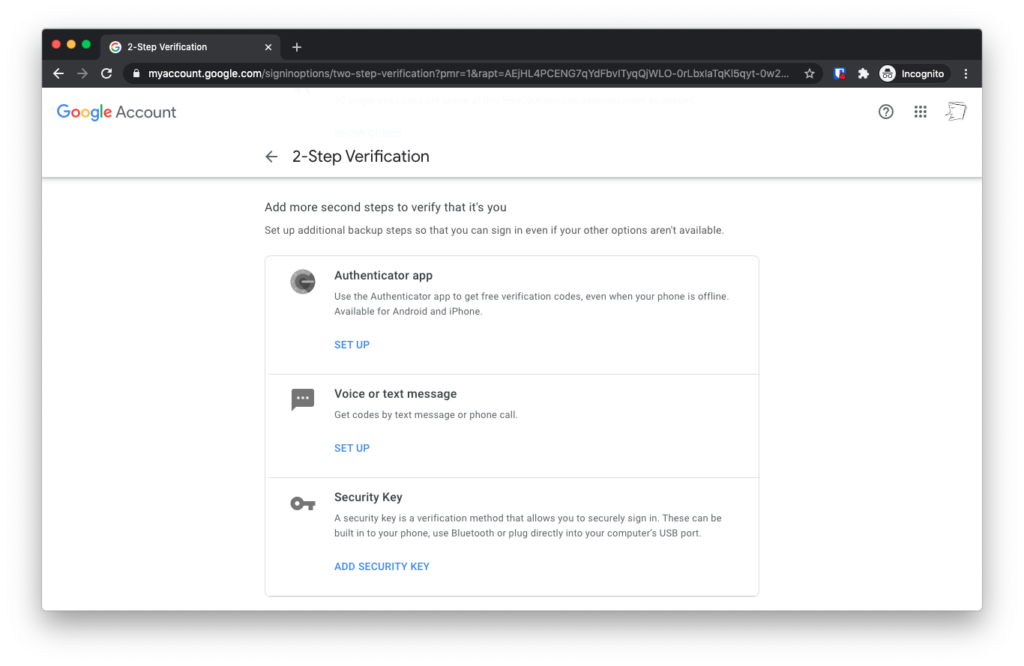
On the next screen, choose whether you have an iPhone or an Android phone. I picked iPhone, but the steps are the same.
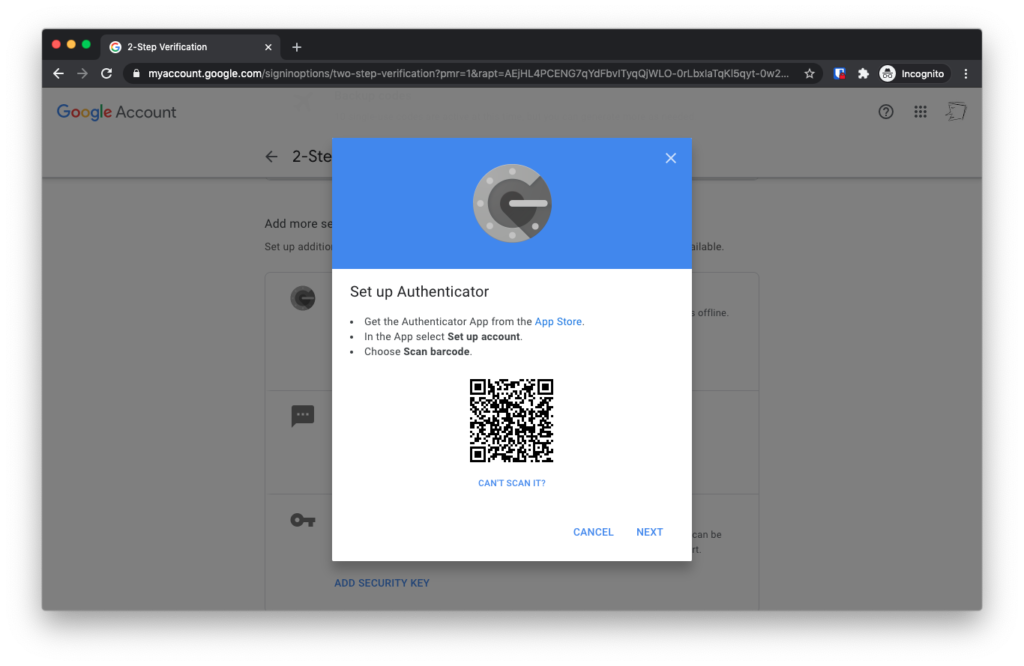
On the next screen, you’ll see a QR Code displayed.
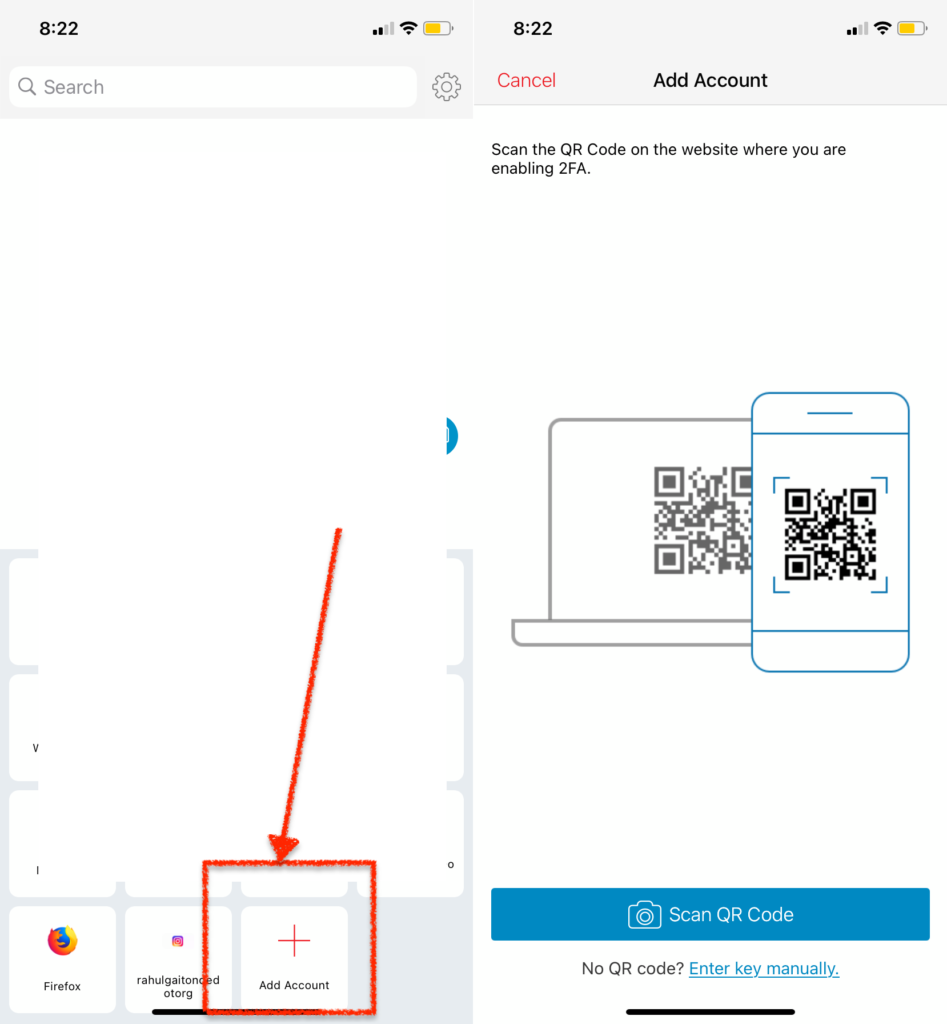
Now on your phone, open the Authy app. Tap “Add Account” and pick “QR Code”.
Scan the QR code on your laptop screen. Your Authy app will immediately identify and add the account. And start displaying six digit codes.
The screen on your browser will automatically refresh to ask for a six digit code. Enter the six digit code that’s displayed on your phone’s Authy screen.
You’re done! Now, when you sign in to Google or Gmail or Google Drive on a new browser on your laptop, or a new app install on your phone, you’ll enter both your username and password, and then the latest six-digit code on your Authy app. That’s it!
Logging into Gmail with your new, secure two-step flow
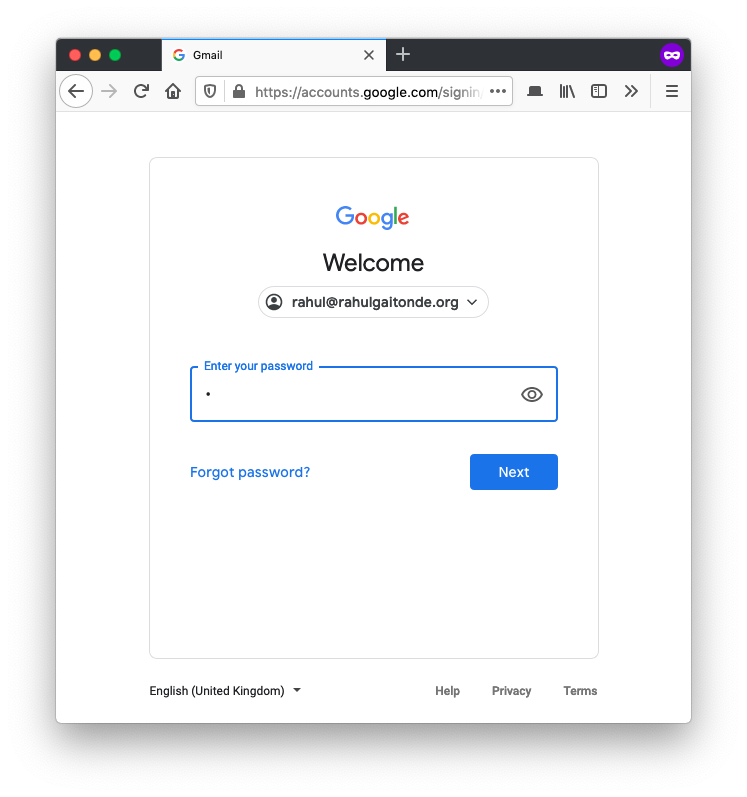
Here is what your new login looks like. First, your user name and password as usual:
Your account’s login screen will then ask you for your second-factor code.
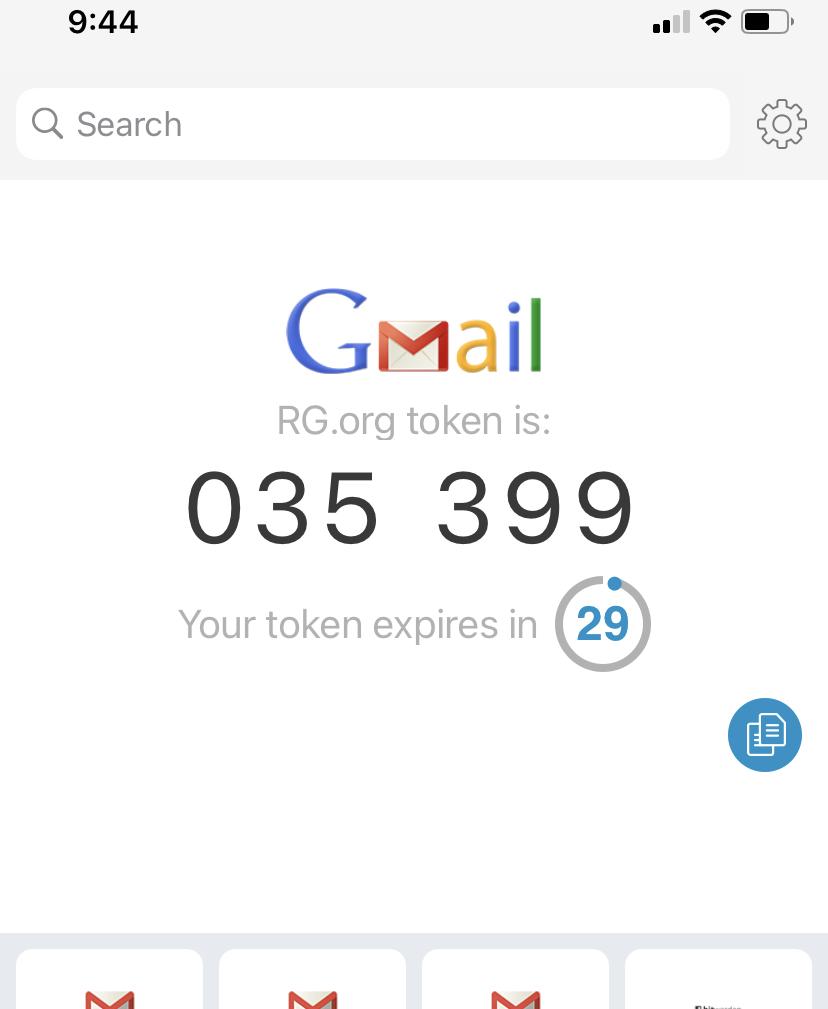
At this point, you look for the code in the Authy app. Authy will generate a code that is valid for a maximum of 30 seconds.
Type this code in the login screen and you’re done!
Why two-factor authentication protects your Gmail account
Let’s go back to the example at the beginning of the post. We saw how you could receive an email that looked very much like it was from Google. It has a link for you to click – the email could say that it was for account management, reviewing and accepting new terms and conditions, or a number of other things.
You don’t review the sender’s email address, which Gmail and other email apps usually collapse, and you need to tap a button to reveal. You think it’s a legitimate email, click on the link, and are taken to a very realistic-looking Google authentication page, asking you for your email address and password, which you enter.
At this point, because the web pages were hosted by a scammer and not by Google, they now have your password. They can now log into Gmail – or your Google Account and prevent you from logging back in.
But if you had 2FA set up, once the scammer entered your email and password into the Google login screen, they would be asked for your second-factor code. They don’t have it. They have no way of going back to you and asking you for another code.
But could they not have asked me for the second-factor code when they displayed the fake pages? Here’s the problem for them: they have no way of knowing in advance if you have two-factor authentication enabled on your account or not.
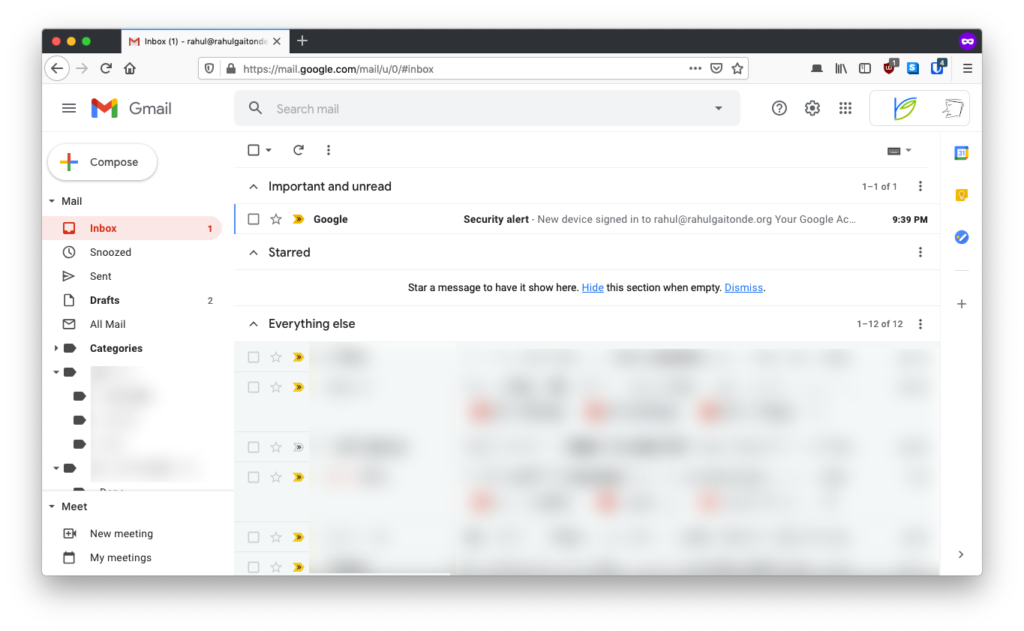
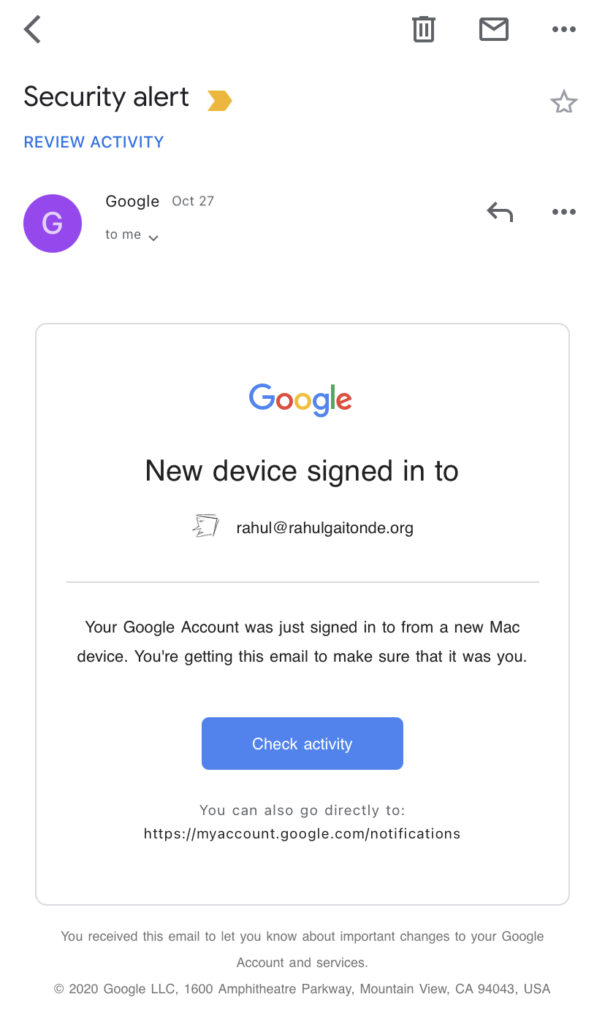
Finally, when they attempt to log in using your (scammed) password, you’ll get an email immediately from Google, which looks like this:
You will know immediately that something is wrong, since this was not you. Once you know this, you can – and should – change your password right away.
(You’d get this email even if you did not have 2FA setup, but by that time it’d be too late, since the attacker would have logged in to your account).
Protecting from really malicious attackers
But what if the scammer was someone who knew you, who is targeting you specifically, who knew – somehow – that you have two-factor turned on, and custom-built a two-factor flow to phish you? A couple of things:
One, your two-factor code is only valid for 30-second intervals. Subtract from that the time it takes for you to look at the code, memorize it, switch back to the login screen, type it (or, if you copied it, then paste it), and tap next. The attacker now needs to copy that code from their malicious code into the Google login screen they’re using to get into your account within whatever few seconds are left. It’s not impossible, but it’s really hard, and even harder to get right in the one shot that they have.
(And it’s not like the 30 second countdown starts when you open the Authy app. Try it – you could well open the app midway through a 30-second cycle, so the time the attacker has is even less).
Two, when you log in with your two factor code on any browser, select the ‘Don’t ask again on this computer’ box on the two-factor screen:
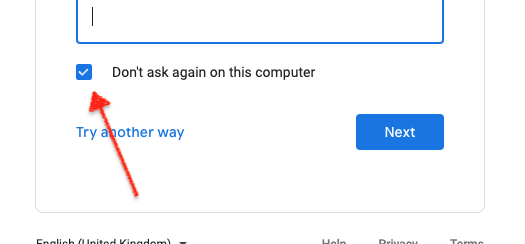
Why would you want to tell the browser to bypass the second factor? Because access to your browser is safe – since it’s on your password-protected phone or computer – and now you can distinguish between a trusted and an untrusted page. How?
Let’s go back to the truly malicious attacker, who has found out beforehand – somehow – that you have set up two-factor authentication, and has created a fake Google-like flow that asked you for your second-factor code. You are fooled by the genuine-looking email, and you click on the link. Your browser opens. You are further fooled by the genuine-looking login page, so you enter your username and password. Now you see a genuine-looking second-factor page.
At this point, you should immediately be suspicious – you’ve explicitly specified to this browser that you don’t want Google to ask you for a second factor code. That should tell you it’s not a genuine web page, and you can pause and check the email and the login page are genuine.
Links to set up two-factor authentication for Instagram, Facebook and other social media
Authy has helpful guides with steps and screenshots for setting up 2FA for many common services. Everything above on how 2FA protects your Gmail account is applicable for all the services below.
If you own an iPhone, Mac or iPad, you should also turn on two-factor authentication for your Apple iCloud account using these instructions. The only difference is that you don’t need to use Authy. Apple will send the second-factor code to one of your devices as a notification.
Remember
- In each case, choose to use an ‘authentication app’ over using ‘SMS’. Add the account to Authy in the same way as in the Gmail example above.
- In each case, save any recovery codes that are displayed on screen. In the rare case that you are locked out of your Authy account AND need to use your second factor for one of your accounts, you can use one of these recovery codes to log in.
So. I hope this gives you a good idea of not just the what, but also the why and how of protecting your accounts with two factor authentication.
If more of us do this, and spread the word, we can defeat phishers and scammers – something unimaginable today.
Appendix: questions I usually get about two-factor authentication
Why not have my second factor sent to me over SMS? Why bother with a whole new app?
After all, this is how the “3D secure” protection works on credit card payments. Your credit card number and expiry are like your username, your CVV is your password, and then the SMS you receive from Visa or Mastercard or American Express or RuPay is your second factor.
The problem is that SMS as second factor is known to be insecure. Motivated attackers have been able to take control of your mobile number itself using a technique commonly known as SIM swap. After such an attack, your SMSes are now sent to their phone instead of yours. This 2020 CNET article describes this method:
Hackers have been able to trick carriers into porting a phone number to a new device in a move called a SIM swap. It could be as easy as knowing your phone number and the last four digits of your Social Security number, data that tends to get leaked from time to time from banks and large corporations. Once a hacker has redirected your phone number, they no longer need your physical phone in order to gain access to your 2FA codes.
The SIM swap vulnerability was in the media last year when Twitter CEO Jack Dorsey’s account was compromised via this method because he had two-factor authentication turned on, but via SMS:
Attackers could simply target the telecom network itself, as this Verge article shows:
Positive Technologies was able to hijack the text messages using its own research tool, which exploits weaknesses in the cellular network to intercept text messages in transit. Known as the SS7 network, that network is shared by every telecom to manage calls and texts between phone numbers. There are a number of known SS7 vulnerabilities, and while access to the SS7 network is theoretically restricted to telecom companies, hijacking services are frequently available on criminal marketplaces.
As of today, it’s unlikely that a casual attacker will resort to SIM swapping or an SS7 attack. But don’t discount malicious attackers – ex employees/teammates, a relationship that ended badly, a competitor, or someone who values access to your email/social media to get info about someone you know.
Why use two-factor codes instead of Google’s default notification system?
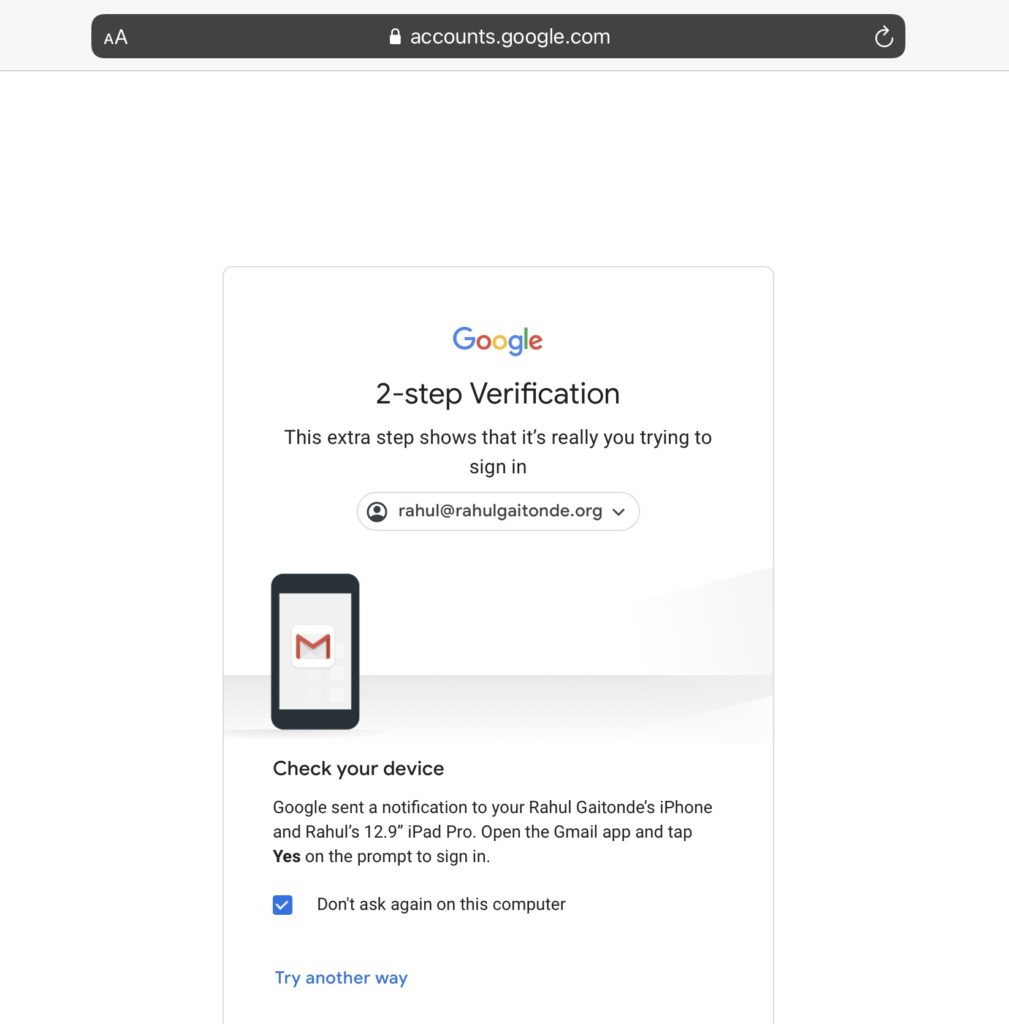
Google today pushes you to use its notification system as your second factor. This doesn’t require you to copy and paste time-sensitive six digits codes, ostensibly making your second factor login experience simpler. This is how it looks. After you enter your email and password, you see this screen:
If you open your Gmail app, it’ll open to this screen:
If you tap yes, your browser proceeds to your Gmail/Google Drive/whatever Google service you were logging into. This works across devices – you could be logging in on your laptop and tap Yes in the Gmail app on your phone.
Clearly there are advantages.
One, you’re not reading and re-typing six digit codes, so there’s no chance you’ll mis-type anything.
Two, it’s a single tap, so it’s much faster – there is no chance that the code will have expired by the time you paste it.
Three, the notification shows you the location of where the login is taking place. If your attacker isn’t in the same city as you, this is an immediate sign something is wrong. Same with the device. If you don’t own a Mac, and the notification shows that the login is taking place on one (like in the screenshot), you’re being phished.
Four, the 2-step verification screen lists the names of your device(s) that have Gmail installed. You can see that the text in the screenshot says “Google has sent a notification to your Rahul Gaitonde’s iPhone and Rahul’s 12.9” iPad Pro”. It’s almost impossible for an attacker to know this level of detail about you, so the fake two-factor screen that they present to you will almost certainly not name your devices.
So why should you use the Authy app instead of this seemingly elegant method?
One, everything we’ve seen above only applies to your Google account. To secure your Instagram, Facebook, Snapchat, Uber and other accounts, you’re going to need a code-based method anyway. Simplify your life. Use one solution instead of many.
Two, there is a real security downside.
Let’s revisit our walk-through of the phishing attempt. You’ve been fooled into clicking on a phishing email, fooled into entering your email and password on a phishing login page. In addition, your attacker, who is targeting you personally, has determined that you do have two-factor on, so they’ve created a page that resembles the 2-step verification screenshot above. As you enter your user name and password, they copy the password into an actual Google login screen, ready to get into your account.
Now, since you’re distracted, it’s likely you’ll fail to notice the location and device in the 2 factor notification in your Gmail app. After all, you haven’t noticed that the email – and these login screens – aren’t genuine. So. If you tap the notification (because you think you are in fact logging in), your attacker is in – instantly.
Contrast this to if you had pasted or typed your two-factor code. As we have seen above, it’s time-sensitive. And therefore
… your two-factor code is only valid for 30-second intervals. Subtract from that the time it takes for you to look at the code, memorize it, switch back to the login screen, type it (or, if you copied it, then paste it), and tap next. The attacker now needs to copy that code from their malicious code into the Google login screen they’re using to get into your account within whatever few seconds are left. It’s not impossible, but it’s really hard, and even harder to get right in the one shot that they have.
(And it’s not like the 30 second countdown starts when you open the Authy app. Try it – you could well open the app midway through a 30-second cycle, so the time the attacker has is even less).
In the case of the Gmail notification, the attacker doesn’t have to do any work. You tap the notification, they’re in. In this case, they have to read, copy, paste the code and tap Go within a tiny unit of time that they don’t know.
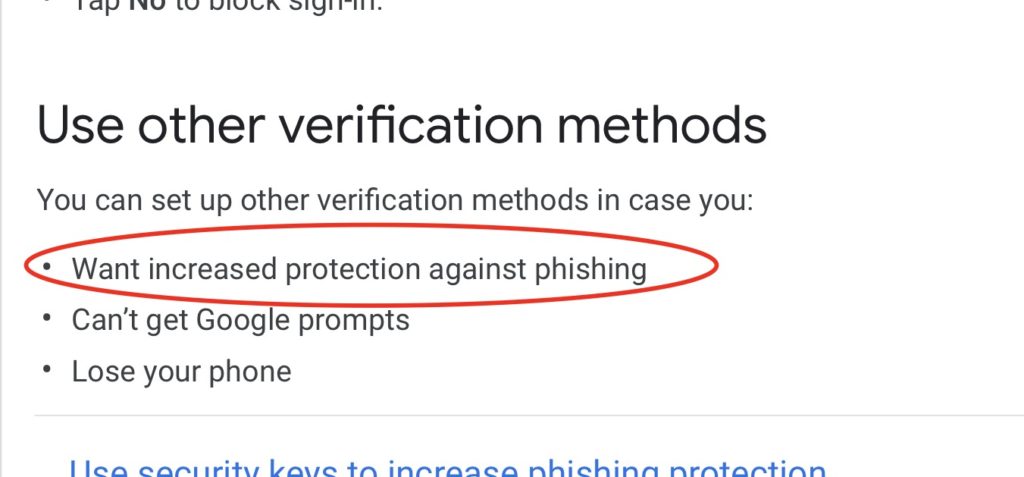
Indeed, Google itself includes this little bit in their two-factor verification guide:
Why use Authy instead of the Google Authenticator app?
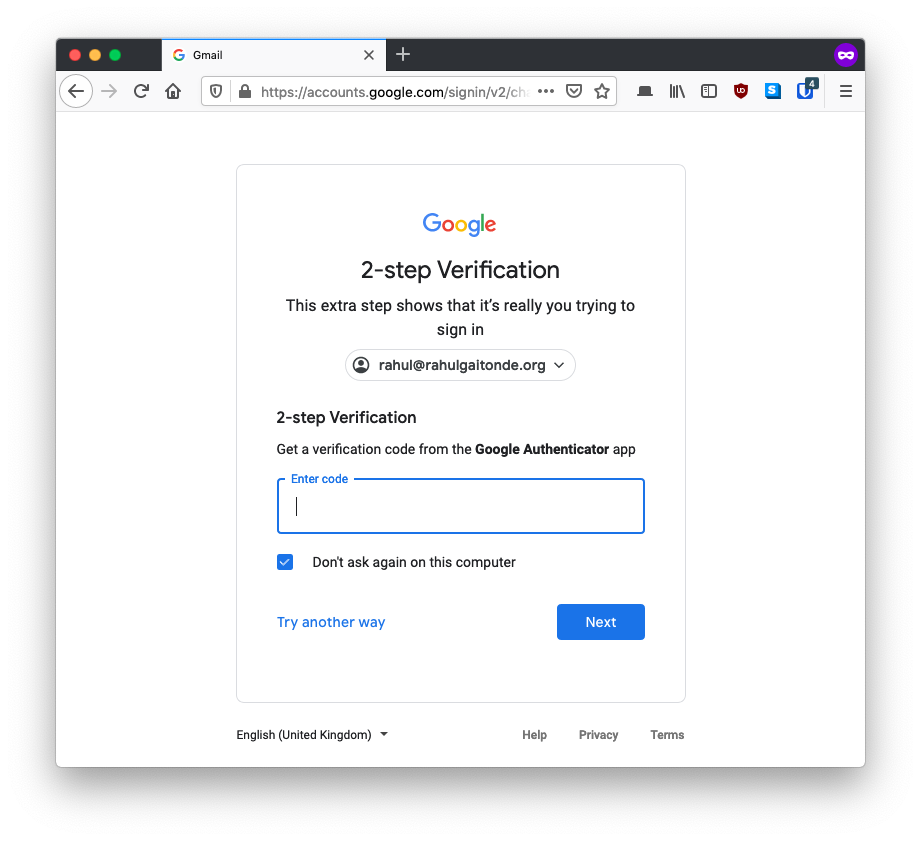
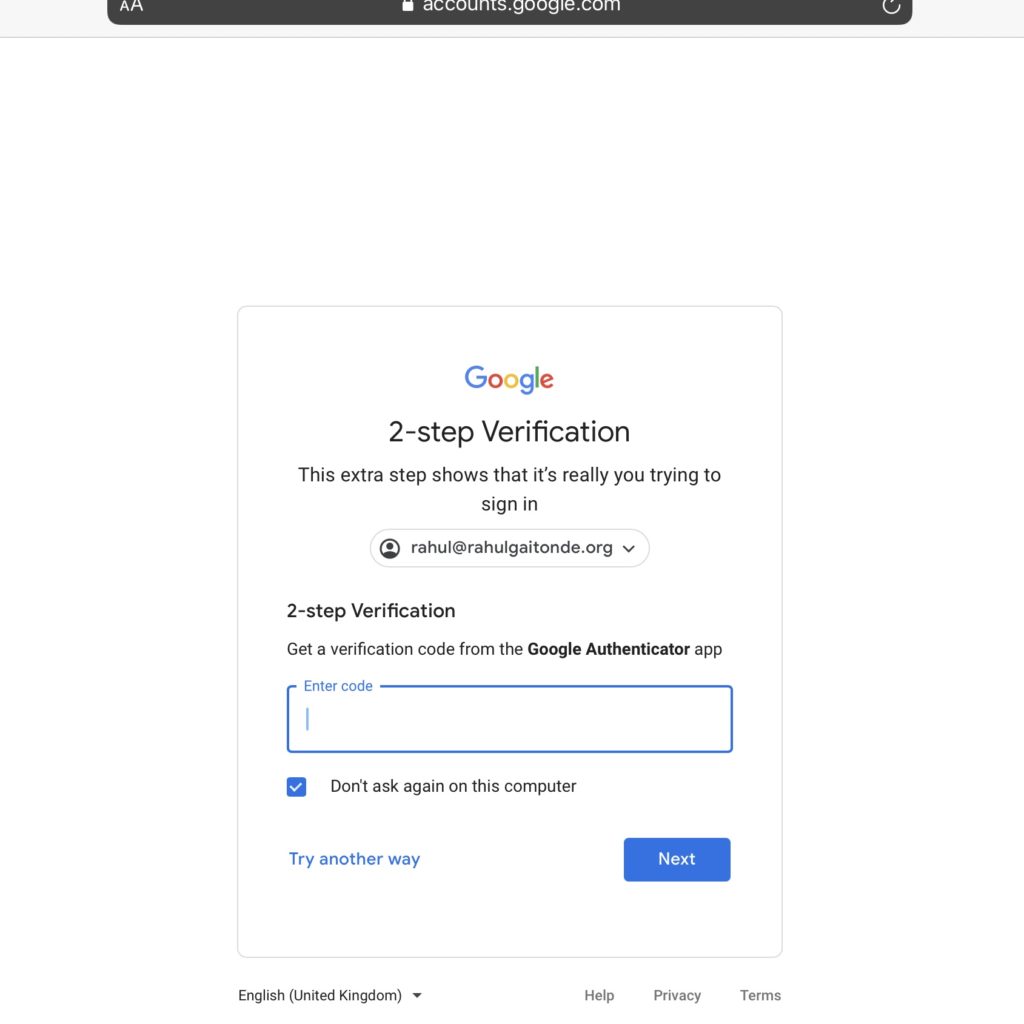
Google’s guides heavily promote their own Authenticator app over others like Authy. Even their code-based two-factor login screen refers only to the Google Authenticator app:
I’ll point you to Authy’s comparison guide, but here are the main bits: Google Authenticator is only available on mobile devices (not Macs or PCs), it can only be installed on one device at a time, it can’t restore from encrypted backups like Authy can.
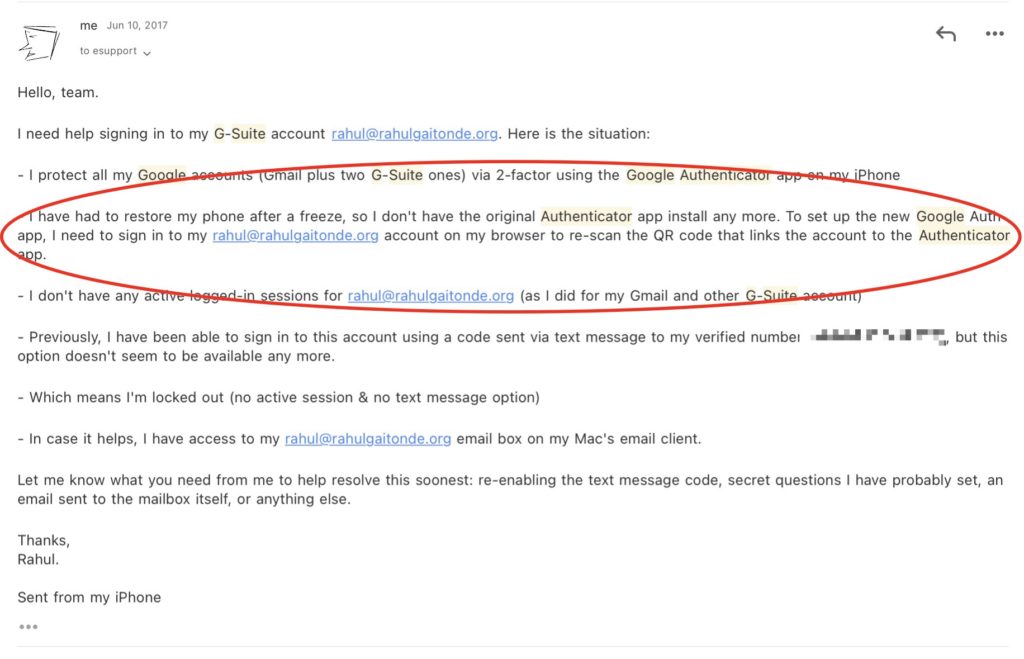
The one-device limitation has caused problems in the past,. Due to a combination of factors, I was once forced to reach out to Google support to restore access to my account:
If I had been able to install Google Authenticator on my iPad or Mac, this wouldn’t have been an issue at all.
There are several 2FA apps available other than Authy. There’s Duo. There’s Microsoft’s Authenticator app. Password managers like 1Password can generate 2FA codes. Why, there are listicles about 2FA apps. Check them out if you like. Google Authenticator and Authy are the only ones I have personally tried and used.
(ends)
Disclosure: I own stock in Twilio, which owns Authy. I have no other relationship with Authy and received no compensation from Twilio/Authy for this article.



2 replies on “Your guide to protecting your Gmail, Instagram, Facebook, Linkedin, Twitter and other accounts from being hacked”
Why does Authy provide this service for free?? Aka how does Authy make money? Like most free services, are we exchanging data for service??
Freemium. Authy also makes the same tech available to companies to build two factor protection into their software: https://www.twilio.com/authy/pricing